18-37
Cisco Prime Network 4.0 User Guide
OL-29343-01
Chapter 18 Monitoring MPLS Services
Monitoring MPLS Services
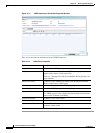
Table 18-15 describes the information that is displayed in the Rate Limits tab of the IP Interface
Properties dialog box.
Viewing VRRP Information
Virtual Router Redundancy Protocol (VRRP) is a non-proprietary redundancy protocol that is designed
to increase the availability of the static default gateway servicing hosts on the same subnet. This
increased reliability is achieved by advertising a virtual router (a representation of master and backup
routers acting as a group) as a default gateway to the hosts instead of one physical router. Two or more
physical routers are then configured to stand for the virtual router, with only one doing the actual routing
at any given time. If the current physical router that is routing the data on behalf of the virtual router
fails, another physical router automatically replaces it. The physical router that forwards data on behalf
of the virtual router is called the master router; physical routers standing by to take over for the master
router if needed are called backup routers.
To view VRRP information:
Step 1 Double-click the required element in Prime Network Vision.
Step 2 In logical inventory, choose Logical Inventory > Routing Entities > Routing Entity.
Step 3 In the IP Interfaces tab, double-click the required interface to view the IP interface properties. If VRRP
is configured on the IP interface, the VRRP Groups tab is displayed.
Table 18-15 Rate Limits Information
Field Description
Type Rate limit direction, either Input or Output.
Max Burst Excess burst size in bytes.
Normal Burst Normal burst size in bytes.
Bit Per Second Average rate in bits per second.
Conform Action Action that can be performed on the packet if it conforms to the specified
rate limit (rule), for example, continue, drop, change a bit, or transmit.
Exceed Action Action that can be performed on the packet if it exceeds the specified rate
limit (rule), for example, continue, drop, change a bit, or transmit.
Access List Hyperlink that highlights the related access list in the Access List table.