Send documentation comments to mdsfeedback-doc@cisco.com.
29-11
Cisco MDS 9000 Family Fabric Manager Configuration Guide
OL-6965-03, Cisco MDS SAN-OS Release 2.x
Chapter 29 IPsec and IKE
Modifying IKE and IPsec
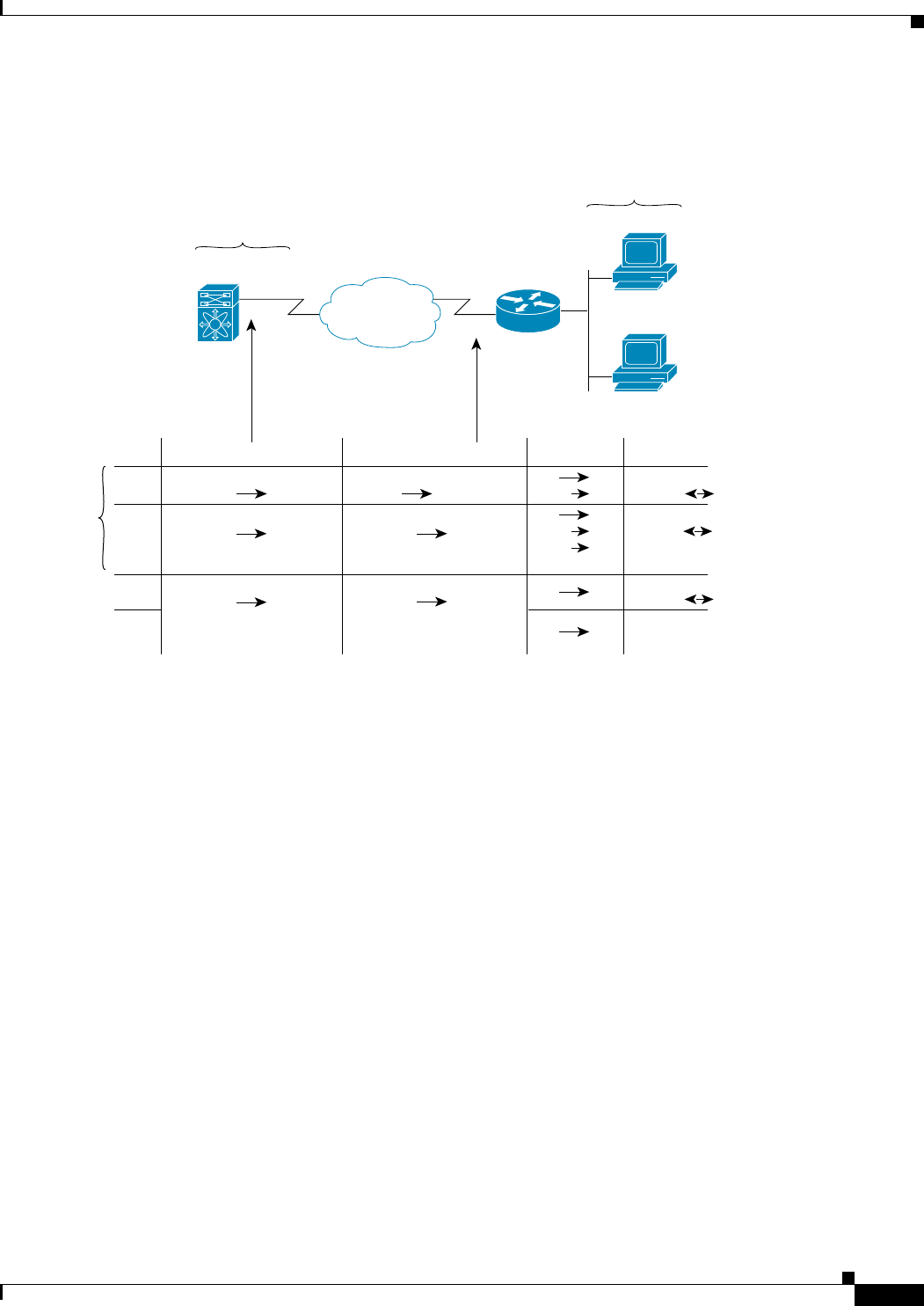
Figure 29-5 shows some sample scenarios with and without mirror image ACLs.
Figure 29-5 IPsec Processing of Mirror Image Configuration
As Figure 29-5 indicates, IPsec SAs can be established as expected whenever the two peers' crypto ACLs
are mirror images of each other. However, an IPsec SA can be established only some of the time when
the ACLs are not mirror images of each other. This can happen in the case where an entry in one peer's
ACL is a subset of an entry in the other peer's ACL, such as shown in Cases 3 and 4 of Figure 3. IPsec
SA establishment is critical to IPsec—without SAs, IPsec does not work, causing any packets matching
the crypto ACL criteria to be silently dropped instead of being forwarded with IPsec security.
In Figure 29-5, an SA cannot be established in Case 4. This is because SAs are always requested
according to the crypto ACLs at the initiating packet's end. In Case 4, switch N requests that all traffic
between Subnet X and Subnet Y be protected, but this is a superset of the specific flows permitted by
the crypto ACL at switch M so the request is therefore not permitted. Case 3 works because switch M's
request is a subset of the specific flows permitted by the crypto ACL at switch N.
Because of the complexities introduced when crypto ACLs are not configured as mirror images at peer
IPsec devices, Cisco strongly encourages you to use mirror image crypto ACLs.
Internet
S0
S1
Switch M Router N
Mirror image
access lists at
Switch M S0
and
Router N S1
IPSec access list at S0
permits
Switch M Host B
permits
Host B Switch M
M B
or B M
SAs established for
Traffic M B (good)
SAs established for
Traffic M B (good)
SAs cannot be
established and
packets from Host
B to Switch M are
dropped (bad)
SAs established for
Traffic X Y (good)
M B
B M
M B
or B M
or M C
permits
Switch M Host B
permits
Subnet X Subnet Y
permits
Subnet Y Subnet X
permits
Subnet Y Subnet X
IPSec access list at S1 1st packet Result
Case 1
Case 2
Case 3
Case 4
120486
Subnet X
Subnet Y
Host B
Host C


















