Send documentation comments to mdsfeedback-doc@cisco.com.
29-10
Cisco MDS 9000 Family Fabric Manager Configuration Guide
OL-6965-03, Cisco MDS SAN-OS Release 2.x
Chapter 29 IPsec and IKE
Modifying IKE and IPsec
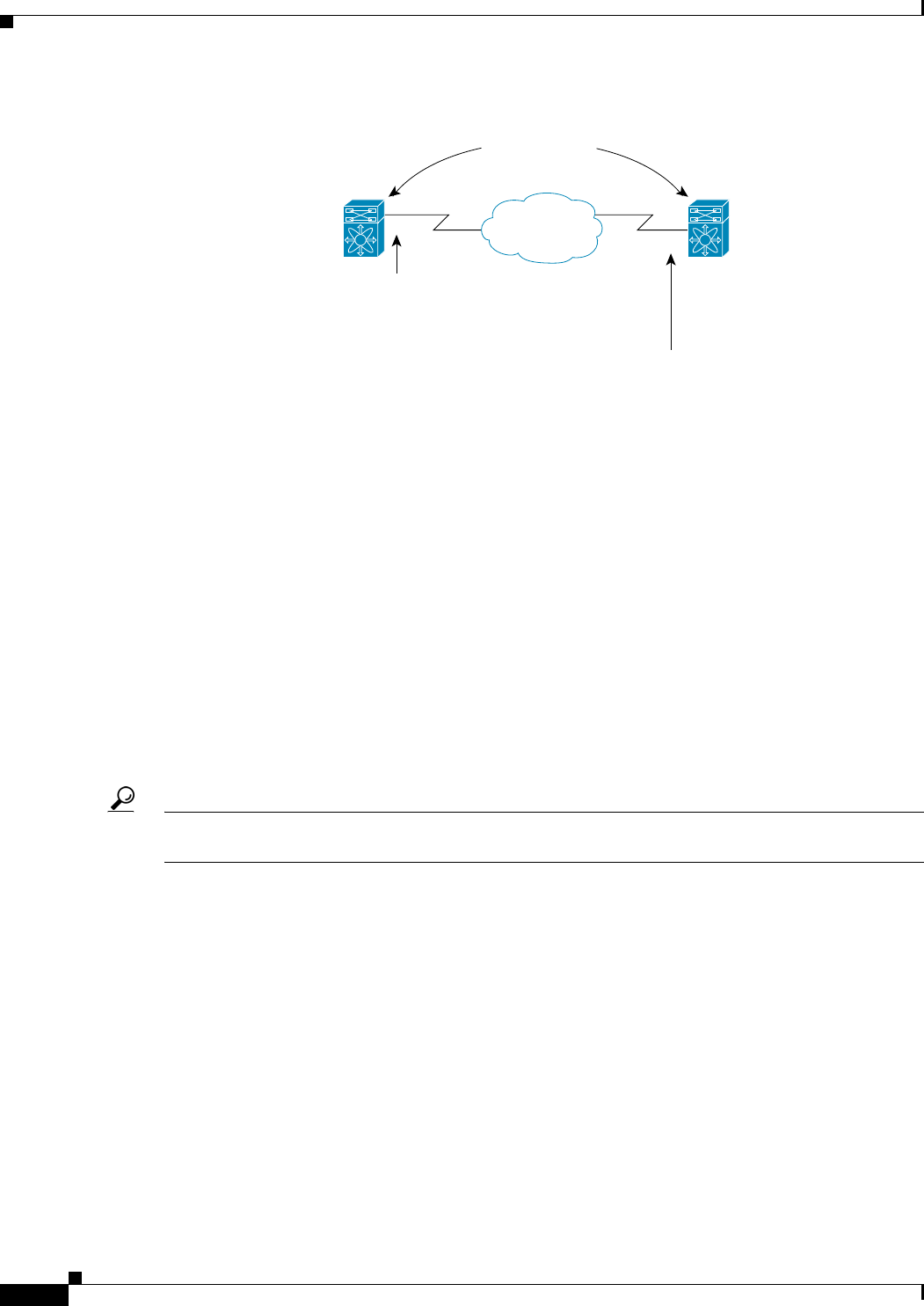
Figure 29-4 IPsec Processing of Crypto ACLS
• If you configure multiple statements for a given crypto ACL which is used for IPsec, the first permit
statement that is matched is used to determine the scope of the IPsec SA. Later, if traffic matches a
different permit statement of the crypto ACL, a new, separate IPsec SA is negotiated to protect
traffic matching the newly matched ACL statement.
• Unprotected inbound traffic that matches a permit entry in the crypto ACL for a crypto map entry
flagged as IPsec is dropped, because this traffic was expected to be protected by IPsec.
• The IP ACLs used for traffic filtering purposes are also used for crypto.
Mirror Image Crypto ACLs
For every crypto ACL specified for a crypto map entry defined at the local peer, define a mirror image
crypto ACL at the remote peer. This configuration ensures that IPsec traffic applied locally can be
processed correctly at the remote peer.
Tip The crypto map entries themselves must also support common transforms and must refer to the other
system as a peer.)
IPSec peers
Internet
S0
S1
IPSec access list at S0:
access-list S0 permit ip 10.0.0.1 0.0.0.255 20.0.0.2 0.0.0.255
IPSec access list at S1:
access-list S1 permit ip 20.0.0.2 0.0.0.255 10.0.0.1 0.0.0.255
Traffic exchanged between 10.0.0.1 and 20.0.0.2 is protected.
120485
MDS_Switch A MDS_Switch N


















